What is a vulnerability?
In the realm of IT, a vulnerability is a known weakness in your current configuration, which can allow unknown and unauthorized access through hardware or software.
What is a Penetration Test?
Penetration testing simulates outside attempts and attacks with the purpose to expose your current network weaknesses and misconfigurations.
Do I need a firewall appliance?
Deploying a firewall appliance provides a dedicated appliance that provides advanced threat protection. PC Solutions offers the best-in-class technology that’s tailored to your specific organization’s needs.
Why are proactive data security services critical?
Due to the number of advanced cyber threats, it is even more vital for every organization to have their own dedicated cybersecurity team that can identify and resolve vulnerabilities to prevent data breaches and hefty fines due to non-compliance. Your organization’s reputation is only as good as the integrity of your data.
What is the difference between Antivirus and Endpoint Security?
- AntiVirus protects against one specific type of vulnerability (Viruses and Malware).
- Endpoint Security tools protect against multiple types of advanced vulnerabilities (Malware, Ransomware, Unauthorized Access) it is a more comprehensive approach to protecting your workstations and systems against the ever-evolving landscape of cyber threats.
What kind of threats should I be aware and concerned with?
Cyber threats can come from both internal as well as external sources.
- Malware is perhaps one of the most common threats; it is any malicious software code providing an open door to your data.
- Ransomware is a specific type of malicious software that locks data and or services until a monetary ransom is paid to the perpetrator of the hack.
- Malicious websites, news headlines, and online ads can lead to malicious websites.
- Denial of Service (DoS) Attacks is a hacker’s attempt to disable or prevent access to technology services such as; email, websites, and any network resources from authorized users.
- Spoofing attacks occur when a hacker falsifies their identity to gain access to a system to steal sensitive information.
- Backdoor is a type of computer vulnerability that hackers can use to bypass normal authentication protocols to gain access to an application or system.
- Phishing aims to target a user to gather sensitive information such as user/account names, passwords, credit card information, etc. by disguising themselves as a legitimate source. Phishing attacks typically come in the form of an illegitimate email or other original looking material on the internet.
- Social Engineering is the coined term for when attackers predominately rely more on direct human interaction to gather sensitive information to gain access to your data, network or accounts.
Why would I be targeted?
Why would a criminal break into a house or a car? Majority of hackers operate with the same mindset; they want access to your information for monetary gain.
- Small Businesses are typically easy targets for hackers. Small businesses typically have minimal Data Protection Mechanisms, allowing hackers to easily gain access without being noticed
- Hackers can compromise your network to use your systems as a tool in other malicious attacks
What is encryption?
A method that scrambles data so that any unauthorized eyes cannot read or translate the data. Essentially encryption puts a lock on your data, and only the people with the right key can unlock it to read or modify your data.
What is the cost of a breach?
- 60% of small businesses fold within six months after a cyber-attack or data breach.
- Financial consequences continue to rise year over year. From 2016 to 2017 global average of cost of cybercrimes rose by 27%.
- 62% of cyber-breach victims are small to mid-size businesses, which are at the greatest risk for an attack. Their level of preparation is low, and the costs of customer notification alone can be enough to do a small company irreparable financial harm.
Where do I start to secure my organization against hackers and cyber threats?
- PC Solutions is here to help – we offer penetration testing, consulting, and compliance services.
- PC Solutions has the expertise to analyze the security of any small business network and deliver the best fitting solutions to safeguard your organization’s assets.
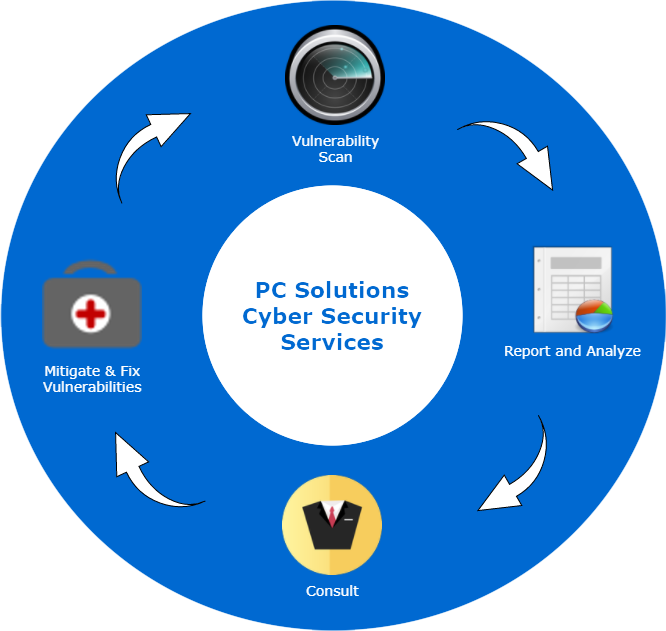
- Flowchart – please see below for example diagram
- 1. Test 2. Report 3. Consult 4. Mitigate and fix